How shipping is so vulnerable to hackers

A week ago Splash reported how consultant Captain Ozgur Dogan Gunes had been able to hack into two Hong Kong shipping lines’ IT systems with just five minutes of casual online browsing. Below he describes some of shipping’s basic cyber security flaws.
The maritime business relies on basic technology to remain connected globally at all times to execute work effectively. However, this can have a disastrous effect on the business if the lines are being compromised.
I’ve recently noticed that a well-known cyber security flaw still exists particularly in the maritime domain. A five-minute curiosity resulted with access to the entire web database with credentials and passwords of two shipowners in Hong Kong operating bulk carriers. Having a website hacked can cause serious consequences especially if it is integrated with no security layers to other systems.
Exploitation of this vulnerability allows hackers to manipulate web documents and also grants advantage to place a backdoor for more catastrophic scenarios if utilised by others. This flaw is explained in examples to keep technical terminology minimum for all parties to understand, exercise and take preventive actions.
The very traditional content of a shipowner website lists fleet information in details of ship particulars.
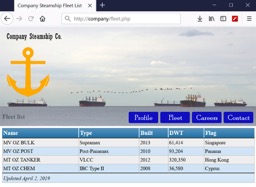
Technically, the data is stored in a table in an ASCII format with a unique ID to identify the rows for SQL statements. Practically, the web interface fetches information from database to show in the screen. This is the fundamental opportunity to access the stored data by triggering different statements at the server with maliciously crafted inputs if there is no security implemented at the server or protected at the design levels.

The hoax in SQL (Structured Query Language) is to include additional parameters to manipulate a database. Example WHERE ID=2 OR 1=1; bypasses the desired record to list all the contents in the table. This can also be practiced at the user level by adding parameters to the link.
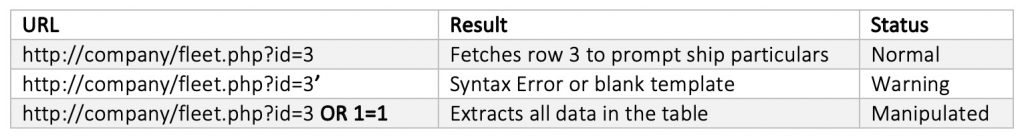
Furthermore, http://company/fleet.php?id=-3 UNION SELECT 1,pass,cc FROM users WHERE username=’admin’ gives the password of the administrator if it is stored in the users table.
The anatomy of this practice is the submission of various unexpected values to observe how the server responds, subsequently to analyse the structure in order to discover a vulnerability in the database management system. This method is widely popular and known as SQL injection that makes it possible to execute malicious statements. There are tools to automate detecting and taking over database servers comfortably in minutes, even for novice users.
The output is clear as crystal.
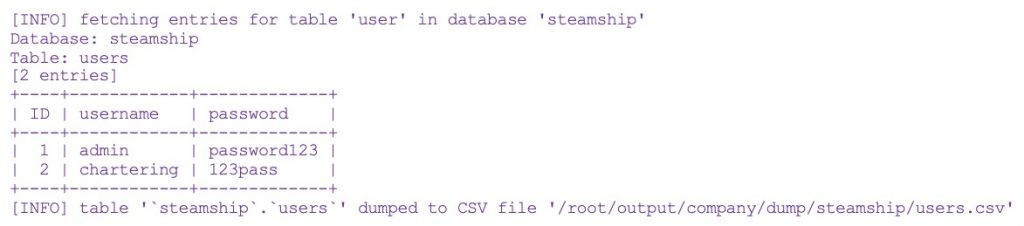
Vulnerability allows hackers not only to spoof identity or tamper the existing with complete disclosure of all data, but also grants shell access which is a vital security hole.
Shell access is basically known as a terminal screen to input commands to reconfigure emails, override passwords, overrule security and upload malicious files. The popular usage of shell access in cyber-attacks is to deploy ransomware to spread among corporate to encrypt data.

The scenarios are infinite when the passwords are clear in text and the same credentials are used in other platforms by employees.
The result is particularly catastrophic if the shell access has been achieved by intruders. Therefore, it is hugely important to develop secured layers between systems and implement procedures with regular updates to remain farther secured. It is a necessity to improve technological initiatives as many of the cloud-based systems continue to have similar injection flaws. Those systems include management applications, PMS, crewing portals, e-learning training solutions, and cargo/voyage/chartering tracking platforms.
Best practice is to implement and develop tailored solutions to better improve work efficiency rather than generic solutions but the following items should be considered as a must at the initial stage,
1. Ensure with codes of webpages not to trigger additional queries
2. Keep webservers, MX records, and other servers separate
3. Encrypt credentials with two factor authentications
4. Use different passwords in each platforms
5. Filter location-based connections
6. Keep software up-to-date
7. Maintain regular back-up
8. Training & procedures
An absolute protection is not possible unless a continuous monitoring provided with decent configuration and procedures. This article is a document proof of known security flaws to support the maritime industry only.

Nicely researched. Thank you.